FAQ about Internet Explorer Enhanced Security Configuration (ESC)
Internet Explorer Enhanced Security Configuration
Internet Explorer Enhanced Security Configuration (ESC) establishes security settings that define how users browse the internet and intranet websites. These settings also reduce the exposure of servers to websites that might present a security risk. This process is also known as IEHarden. For more information, see Internet Explorer:Enhanced Security Configuration.
Original product version: Internet Explorer Original KB number: 4551931
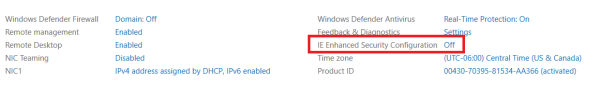
The default setting for Internet Explorer ESC
This feature is enabled by default on servers.
The effects of enabling Internet Explorer ESC
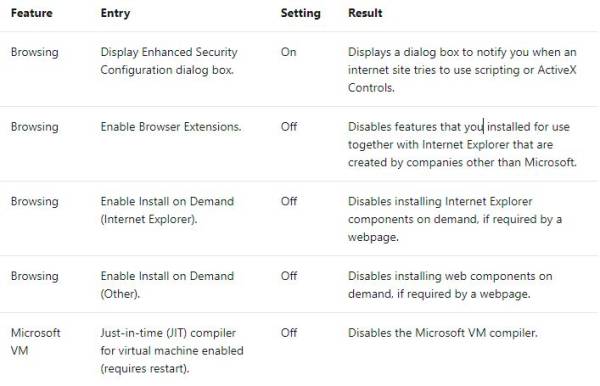
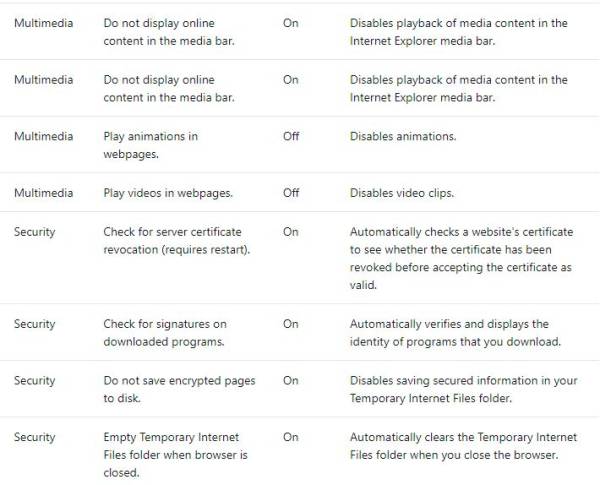
Internet Explorer ESC adjusts the Internet Explorer extensibility and security settings to reduce exposure to possible future security threats. These settings are on the Advanced tab of Internet Options in Control Panel. The following table describes the settings.
These changes reduce the functionality in webpages, web-based applications, local network resources, and applications that use a browser to display online help, support, and general user assistance.
How to turn off Internet Explorer ESC on Windows servers
To turn off Internet Explorer ESC, follow these steps:
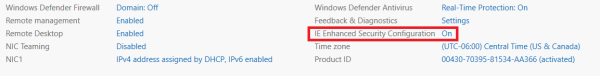
1. Enter Server Manager in Windows search to start Server manager application.
2. Select Local Server.
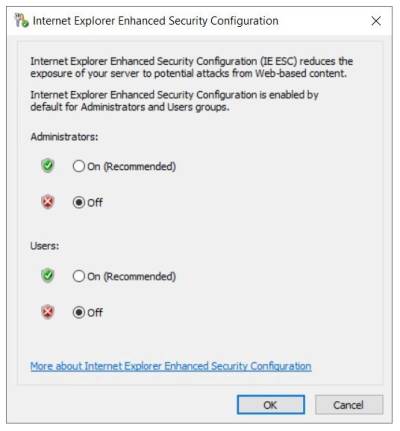
3. Navigate to the IE Enhanced Security Configuration property, select the current setting to open the property page, select the Off option button for the desired users, and then select OK.
4. Select the Refresh icon on the Server Manager toolbar to see the new settings reflected in the server manager.
The following video demonstrates this procedure.
For more information, see Manage the Local Server and the Server Manager Console.
How to disable Internet Explorer ESC by using a script
1. Create an IEHArden_V5.bat file with the following batch file content.
2. Run the bat file either at an administrative command prompt or as part of log-in script by using the procedure that is documented at How to assign user logon scripts.
Contents of the batch file
ECHO OFF
REM IEHarden Removal Project
REM HasVersionInfo: Yes
REM Author: Axelr
REM Productname: Remove IE Enhanced Security
REM Comments: Helps remove the IE Enhanced Security Component of Windows 2003 and 2008(including R2)
REM IEHarden Removal Project End
ECHO ON
::Related Article
::933991 Standard users cannot turn off the Internet Explorer Enhanced Security feature on a Windows Server 2003-based terminal server
::http://support.microsoft.com/default.aspx?scid=kb;EN-US;933991
:: Rem out if you like to Backup the registry keys
::REG EXPORT "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A7-37EF-4b3f-8CFC-4F3A74704073}" "%TEMP%.HKEY_LOCAL_MACHINE.SOFTWARE.Microsoft.Active Setup.Installed Components.A509B1A7-37EF-4b3f-8CFC-4F3A74704073.reg"
::REG EXPORT "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A7-37EF-4b3f-8CFC-4F3A74704073}" "%TEMP%.HKEY_LOCAL_MACHINE.SOFTWARE.Microsoft.Active Setup.Installed Components.A509B1A8-37EF-4b3f-8CFC-4F3A74704073.reg"
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A7-37EF-4b3f-8CFC-4F3A74704073}" /v "IsInstalled" /t REG_DWORD /d 0 /f
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A8-37EF-4b3f-8CFC-4F3A74704073}" /v "IsInstalled" /t REG_DWORD /d 0 /f
::x64
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432node\Microsoft\Active Setup\Installed Components\{A509B1A8-37EF-4b3f-8CFC-4F3A74704073}" /v "IsInstalled" /t REG_DWORD /d 0 /f
::Disables IE Harden for user if set to 1 which is enabled
REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap" /v "IEHarden" /t REG_DWORD /d 0 /f
REG ADD "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap" /v "IEHarden" /t REG_DWORD /d 0 /f
REG ADD "HKEY_CURRENT_USER\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap" /v "IEHarden" /t REG_DWORD /d 0 /f
::Removing line below as it is not needed for Windows 2003 scenarios. You may need to enable it for Windows 2008 scenarios
::Rundll32 iesetup.dll,IEHardenLMSettings
Rundll32 iesetup.dll,IEHardenUser
Rundll32 iesetup.dll,IEHardenAdmin
Rundll32 iesetup.dll,IEHardenMachineNow
::This apply to Windows 2003 Servers
REG DELETE "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" /v "iehardenadmin" /f /va
REG DELETE "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" /v "iehardenuser" /f /va
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" /v "iehardenadmin" /t REG_DWORD /d 0 /f
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\OC Manager\Subcomponents" /v "iehardenuser" /t REG_DWORD /d 0 /f
::REG DELETE "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A7-37EF-4b3f-8CFC-4F3A74704073}" /f /va
::REG DELETE "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A8-37EF-4b3f-8CFC-4F3A74704073}" /f /va
:: Optional to remove warning on first IE Run and set home page to blank. remove the :: from lines below
:: 32-bit HKCU Keys
REG DELETE "HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main" /v "First Home Page" /f
REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main" /v "Default_Page_URL" /t REG_SZ /d "about:blank" /f
REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main" /v "Start Page" /t REG_SZ /d "about:blank" /f
:: This will disable a warning the user may get regarding Protected Mode being disable for intranet, which is the default.
:: See article http://social.technet.microsoft.com/Forums/lv-LV/winserverTS/thread/34719084-5bdb-4590-9ebf-e190e8784ec7
:: Intranet Protected mode is disable. Warning should not appear and this key will disable the warning
REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main" /v "NoProtectedModeBanner" /t REG_DWORD /d 1 /f
:: Removing Terminal Server Shadowing x86 32bit
REG DELETE "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap" /v "IEHarden" /f
:: Removing Terminal Server Shadowing Wow6432Node
REG DELETE "HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap" /v "IEHarden" /f
How to manage the IEHarden Setting for users by using Group Policy Preferences (GPP)
To change the IEHarden setting for users by using Group Policy Preferences Registry configuration, follow these steps:
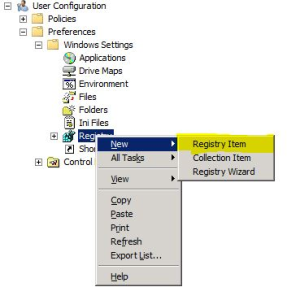
1. Open the GPMCM.msc console, and then navigate to User Configuration > Preferences > Windows Settings.
2. In the navigation pane, right-click the Registry object, and then select New > Registry Item.
3. In IEHarden Properties, specify the following settings:
- Location: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
- Value name: IEHarden
- Value Type: REG_DWORD
- Value data: 0 or 00000000
Select Apply and OK to complete this GPP configuration.
Note: You may also want to check the following registry subkeys if this value does not resolve the problem. In most cases, this is not necessary. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap HKEY_CURRENT_USER\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
Internet Explorer doesn't seem to work after you disable ESC by using Server Manager
To troubleshoot this scenario, refer to Standard users can't turn off Internet Explorer Enhanced Security feature on a Windows Server 2003-based terminal server or a later version. Basically, you may have to enable or disable ESC again. Targeting the registry may be the easiest way to resolve this problem.